San Francisco transit system hijacked by ransomware attack
Commuters in San Francisco were treated to a free ride over the weekend after hackers shut down system

On Saturday, users of San Francisco's Munitransit system were treated to a free ride when hackers took down theticketing system.
The hackers used a form ofransomware, a type of computermalware. The malicious softwareeither locks or encrypts a user'sdata, and the hackers demand a ransom to restore theinformation. Typically, the user is alerted to such an attack by an on-screen message.
Muni computer hack caused payment machines to shut down https://t.co/X2ulDWnkB2 pic.twitter.com/4Qg3PKDmAl
—@SF_CA_RRIn the case of Muni, the message the hackers left across the ticketing systemwas, "You hacked, ALL Data Encrypted." They demanded payment of 100 Bitcoin, which adds up to about $70,000 US ($94,600 Cdn).
This isn't the first large-scale attack involving ransomware. In early 2016, a joint statement was released by both the U.S. and Canadian governments after hackers used ransomwareto infect computers belonging to healthcare facilities and hospitals in the U.S., Germany and New Zealand.
- The Canadian government doesn't want hackers' help
- Yahoo confirms 500 million email accounts hacked in 2014
The Muni ransomware infection is believed to be tied to malware known as HDDCryptor. This uses sophisticated coding that encrypts an entire network and overwrites the Master Boot Record of the machine,which can then make the system reboot in order todisplay its ransom message.
It seems that this weekend's attackwasn'ttargeted to the transit system, but a random attack. Essentially, it found a weaknessand hijacked the system.
The message from the hackers, in broken English, gave no indication of the purpose of the hack.
"We don't attention to interview and propagate news! Our software working completely automatically and we don't have targeted attack to anywhere! SFMTA network was Very Open and 2000 Server/PC infected by software! So we are waiting for contact any responsible person in SFMTA but I think they don't want deal! So we close this email tomorrow!" was the message sent by cryptom27@yandex.com. The address has been used in other ransomware attacks.
In a statement to the CBC, Paul Rose,chief spokesperson said, "Upon discovering the malware, we immediately contacted the Department of Homeland Security (DHS) to identify and contain the virus.
"The SFMTA has never considered paying the ransom. We have an information technology team in place that can restore our systems and that is what they are doing."
"There's no impact to the transit service, but we have opened the fare gates as a precaution to minimize customer impact," Muni spokesperson Paul Rose told the media on Saturday. "Because this is an ongoing investigation, it would not be appropriate to provide additional details at this point."
How it can happen
Ransomware attacks are lucrative.
"It's a business for itself, unfortunately," saidAttyMashatan, assistant professor atRyersonUniversity's School of Information Technology Management.
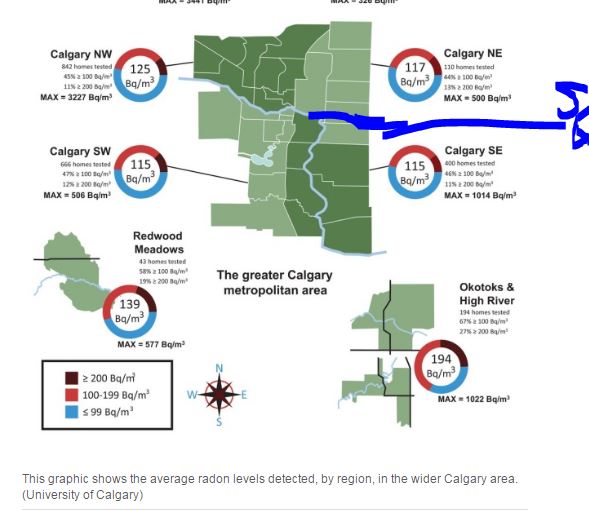
In June, theUniversity of Calgary paid $20,000after a ransomware attack on its computer system.
According to the United States Computer Emergency Readiness Team, in 2012, Symantec, which makes security softwarefor computers, estimated that in one such attack on 5,700 computers, 2.9 per cent of those affectedpaid the ransom, which averaged about $200. That means the hackers made awhopping $349,400 in one month.
The attackers are becoming more sophisticated and better.- AttyMashatan, Ryerson University's School of Information Technology Management
These types of attacks may seem more prevalent these days, but Mashatan said that it's important to look at it from a different perspective: We use computer technology to do much more than we did in the past, everything from banking to shopping.
"We're giving more opportunity to the attacker," she said.
"It's not thatwe're becoming worseor less capable of securing our computer systems. Quite the contrary: We're becoming better and more sophisticated. But the attackers are becoming more sophisticated and better ... It's a catching-up game we're playing all the time."
These ransomware attacks are able to be spread for two reasons: advancing computer technology that isn't adequately protecting systems, but also human error.
While this generation and the one before grew up with tech words like "malware," "trojans," "bots" and "spyware," there are older generationsthat weren't properly educated about such computer attacks. And, Mashatan said, unfortunately, they are usually the ones facing such threats. Their lack of knowledge can even spread to companies where they work, such as the San Francisco Muni system. All it takes is a click on a malicious link.
The key to preventing such attacks at the very least minimizing them is educating employees and the public. Don't open any suspicious attachments, and question e-mails that may seem odd or out of place.
In the meantime, companies such as the San Francisco Munisystem and other victims to ransomware attacks like the University of Calgary, hospitals and many others, need to better protect themselvesand their clients. As well, governmental agencies need to work together with companies to ensure a safer technological experience, Mashatan said.
Karine Martel, spokesperson with Public Safety Canada told the CBC: "Cyber threats, such as ransomware, are meant to scare and intimidate. If an organization is being targeted, we do not recommend paying the ransom. Even if payment is submitted, there is no guarantee that victims will regain access to their systems."
Martelsaid the agency recommends backing up data on an external drive.
If you've been targeted by a ransomware attack, contact the Canadian Anti-Fraud Centre at 1-888-495-8501 or by email at info@antifraudcentre.ca before paying the ransom.











_(720p).jpg)


 OFFICIAL HD MUSIC VIDEO.jpg)
.jpg)